Digital Personal Data Protection Bill 2023 in India: A Comprehensive Guide
The Union Cabinet has given its nod to the Digital Personal Data Protection (DPDP) Bill 2023 draft, which will be introduced in the upcoming monsoon session of Parliament (July 20 to August 11).
The main objective of the bill is to lay down a holistic legal framework that governs the collection, storage, processing, and transfer of personal data by entities, both governmental and private, operating within the boundaries of India.
The bill mandates the payment of fines for non-compliance with requirements such as seeking consent for the processing of data, making it crucial for organizations that handle personal data to understand how it will work.
This blog will tell you everything you need to know about the bill and provide useful steps that will help your organization prepare for its implementation.
Understanding the Key Aspects of the Bill
The DPDP Bill is all about protecting personal data in the digital age. It applies to any data about an individual that can identify them, whether it’s collected online or offline and then digitized.
The DPDP Bill extends its reach to digital personal data processing that happens outside India, but only if it involves profiling or offering goods/services to individuals within India. In other words, any organization in any part of the world, which handles the personal data of Indian citizens, has to adhere to it.
Now, let’s discuss the responsibilities of those who handle personal data, known as data fiduciaries. First, they must process personal data lawfully and with the consent of the person it belongs to, also known as the data principal. They need to clearly communicate what kind of personal data they collect and for what purposes. And when it comes to children, they must get verifiable consent from their parents. If they don’t follow these rules, they could face penalties.
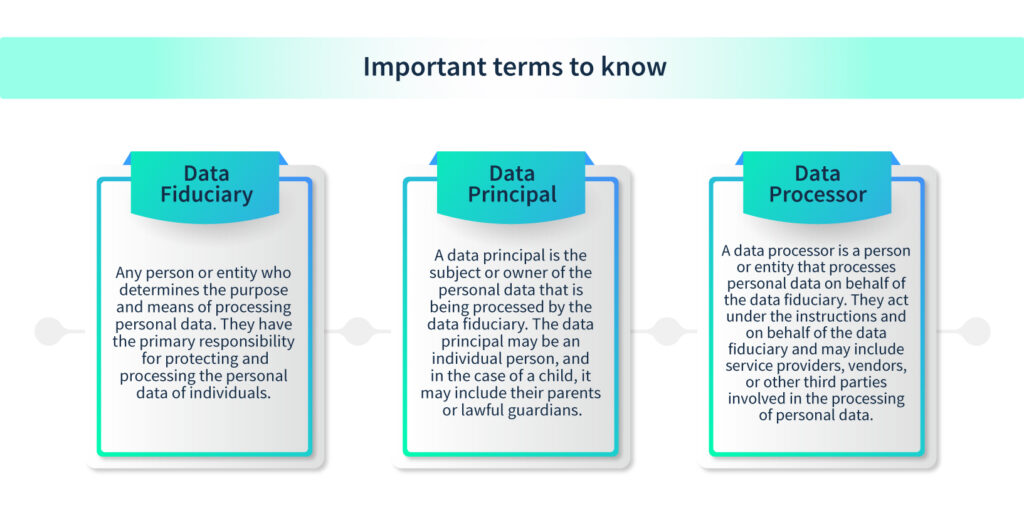
The DPDP Bill takes data breaches seriously. Both the data fiduciary and any data processor they work with must notify the Data Protection Board and the affected individuals in case of a breach.
Data principals, the individuals whose personal data is being processed, have certain rights under the DPDP Bill. Some of these rights include:
A) The right to know if their data is being processed
B) The right to know what kind of data is involved
C) The right to know who it’s being shared with
D) The right to request corrections or deletions if the data is no longer necessary
If they’re not satisfied with how their concerns are addressed, they can file a complaint with the Data Protection Board.
Provisions of the Bill
This DPDB Bill 2023 will extend its legal umbrella to cover all online data (and offline data which is digitized) in India, ensuring comprehensive protection for personal information.
The contents of the Bill, the first draft of which was published in July 2018, will only be disclosed after the Parliament session.
Here is a look at the key highights of the bill based on what we learnt from the previous draft:
Government supervision
A Data Protection Board, established by the Union government, will regulate personal data matters, primarily enforcing compliance and imposing penalties. The government will influence the board’s composition, terms of service, and overall implementation of the law.
Data storage
Unlike previous laws, the draft bill doesn’t require exclusive data storage in India but restricts cross-border data transfer to countries authorized by the Indian government.
Monetary penalties
The draft bill allows only monetary penalties for breaches or non-compliance, ranging from INR 50 crore to INR 250 crore, with a maximum penalty of INR 500 crore for significant data breaches.
Data of minors
Parental consent is mandatory for individuals under 18, although concerns exist about differentiating consent between toddlers and adolescents, the potential impact on personal development, and the violation of the Rights of the Child.
Data collection
Specific limitations on data collection have been removed, allowing data fiduciaries to collect personal data with the consent of the data principal while informing them of the relevant purpose for data collection.
Government exemptions
Government bodies can be exempted from regulations for reasons such as sovereignty, security, foreign relations, and public order, without specific criteria for exemptions.
Limited information requirements
The draft narrows the scope of information provided to data principals, focusing on personal data sought and the purpose of data processing, rather than extensive rights, grievance mechanisms, retention time, and data sources.
Missing provisions
It should be noted that the draft lacks the inclusion of two important provisions:
Data portability
The right to data portability empowers data principals to access and examine their personal data in a structured format. It enables them to choose the platforms on which they want their data to be shared, eliminating the hassle of providing all their personal data again when switching platforms.
Foregone information
The omission of the right to foregone information creates confusion between the general right to erasure and the right to be forgotten, which could potentially undermine freedom of speech and expression for others.
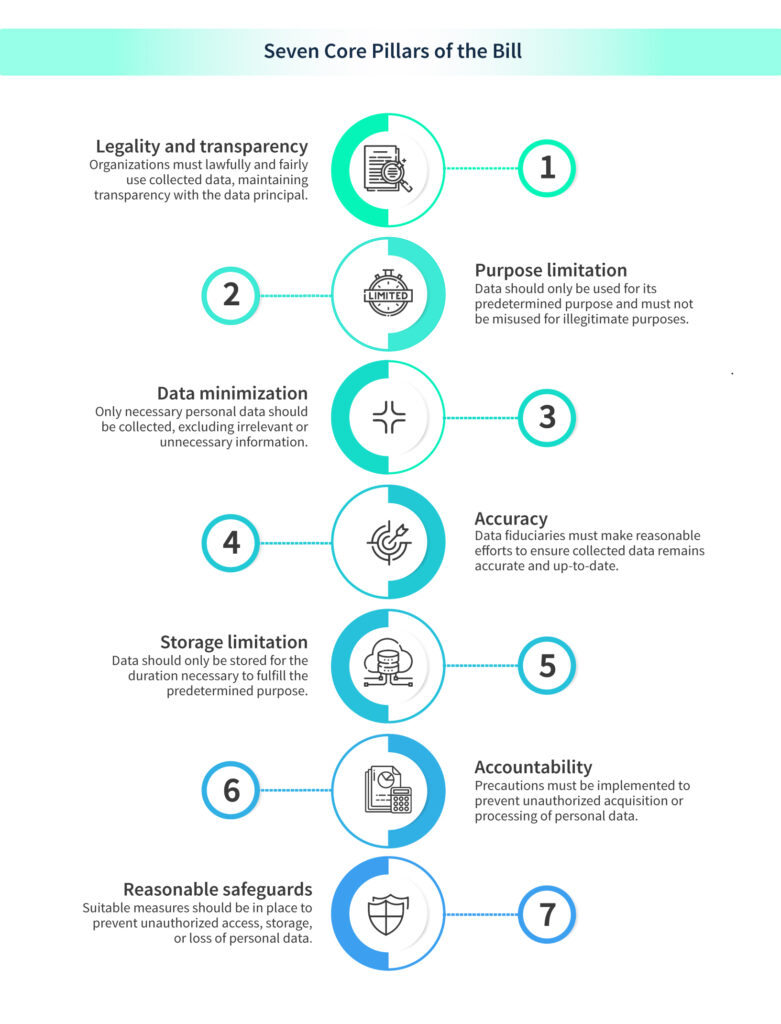
Seven Core Pillars of the Bill
How it will affect Businesses and Organizations
The Data Protection Bill will have significant impacts on businesses and organizations that collect and process the personal data of Indian citizens. Here are some key areas of impact:
Compliance and Legal Obligations
The bill establishes compliance requirements and legal obligations for data-handling entities. Businesses and organizations will need to ensure they adhere to these obligations, such as obtaining consent for data processing, maintaining data accuracy, implementing security measures, and establishing mechanisms for data breach notification. Non-compliance can result in penalties and reputational damage.
Data Governance and Accountability
Robust data governance practices and accountability is a requisite of the bill. Organizations will need to establish policies and procedures for data handling, including data minimization, purpose limitation, and storage limitation. They will also need to appoint Data Protection Officers and demonstrate accountability in their data processing activities.
Consent Management
Obtaining valid consent from individuals for processing their personal data is mandated by the bill. Businesses and organizations will need to review their consent management practices to ensure they meet the bill’s requirements. They will also need to provide clear and transparent information to individuals regarding the purpose and extent of data processing.
Data Localization and Cross-Border Transfers
The bill addresses the issue of data localization, specifying that certain categories of personal data may need to be stored within India. This may impact businesses that operate across borders or rely on international data transfers. They will need to evaluate their data storage and transfer practices to ensure compliance with the bill’s provisions.
Impact on Business Models and Innovation
The bill’s provisions may require businesses and organizations to make changes to their existing business models and data processing practices. It may impact data-driven innovation, as stricter regulations and requirements may introduce additional complexities and limitations on data usage. Organizations will need to assess the impact on their operations and adapt accordingly.
Increased Focus on Data Security
The enforcement of proper data security and protection is highlighted by the bill. Businesses and organizations will need to implement appropriate technical and organizational measures to safeguard personal data from unauthorized access, breaches, and misuse. They may need to invest in robust cybersecurity infrastructure and regularly review their security practices.
Steps to take in preparation for DPDP Bill implementation
In order to be prepared for the bill’s implementation, organizations can take the following steps.

Conduct a data audit
Start by conducting a comprehensive audit of the personal data your organization collects, processes, and stores. Identify the types of data you handle, the purposes of processing, and the legal basis for processing.
Review and update policies
Review your existing privacy policies, consent mechanisms, and data-handling procedures. Update them to align with the requirements of the data protection bill, including provisions on consent, data minimization, purpose limitation, and data subject rights.
Implement strong data governance
Establish robust data governance practices within your organization. This includes defining roles and responsibilities for data protection, appointing a Data Protection Officer (if required), and implementing internal policies and procedures to ensure compliance with the bill’s provisions.
Obtain valid consent
Review your consent management processes to ensure they meet the bill’s requirements. Implement mechanisms to obtain valid and informed consent from individuals, clearly explaining the purpose, extent, and duration of data processing. Ensure individuals can easily withdraw consent if they choose to do so.
Enhance data security measures
Strengthen your data security measures to protect personal data from unauthorized access, breaches, and misuse. Implement appropriate technical and organizational safeguards, such as encryption, access controls, regular vulnerability assessments, and employee training on data security best practices.
Develop a data breach response plan
Prepare a comprehensive data breach response plan that outlines the steps to be taken in case of a data breach. This includes timely identification and assessment of breaches, notification procedures for affected individuals and the Data Protection Board, and remedial actions to mitigate harm and prevent future incidents.
Conduct employee training
Educate your employees about the provisions of the data protection bill and their roles and responsibilities in ensuring compliance. Provide regular training sessions on data protection principles, privacy best practices, and the organization’s data-handling policies.
Establish vendor management processes
Review and update contracts with third-party vendors or processors to ensure they comply with the data protection bill’s requirements. Implement robust vendor management processes, including due diligence, contractual safeguards, and periodic assessments of their data protection practices.
Develop data subject rights procedures
Establish procedures for handling data subject rights requests, such as access, correction, erasure, and objection. Ensure these procedures are efficient, transparent, and compliant with the bill’s timelines and requirements.
Stay updated and seek legal advice
Regularly monitor updates and guidance from the Data Protection Board and relevant authorities regarding the interpretation and enforcement of the data protection bill. Consider seeking legal advice to ensure ongoing compliance and to address any specific concerns or questions related to your organization’s operations.
How We can help you
At CySYS, we have extensive experience in assisting companies with compliance across various frameworks. While the DPDP Bill is yet to be passed, we are fully prepared to help you navigate its requirements. Our expertise extends to compliance with GDPR, ISO 27001, SOC 2, and many other frameworks, making us well-equipped to assist you in preparing for the DPDP Bill.
We understand the challenges that come with regulatory compliance, and our aim is to make the process as seamless as possible for you. Whether it’s implementing the necessary security controls or managing your vendors, we will guide you through every step. If you’re seeking the support of experienced professionals to navigate this new framework, feel free to reach out to us. We’re here to help!


